Introduction
Image to have the following situation:
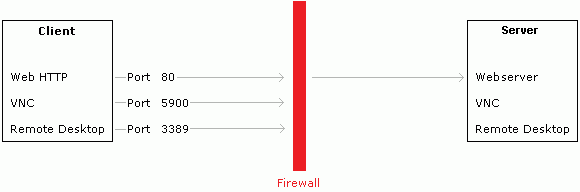
A computer, called
Client, is protected by a firewall, which blocks all the outgoing ports, except some of them. Another computer, called
Server, is outside the firewall, and it's running some services which you want to connect to from the client, like VNC or Microsoft Remote Desktop. Due to the firewall, which blocks all the ports except the number 80 and probably a few others, it's impossible to create a connection between the two pcs.
Assuming that at least another port is opened on the firewall, you can think about using this solution: create a
tunnel between the client and the server using the
SSH Protocol. In short, this is what you'll do:
- The VNC or Remote Desktop clients will connect to an SSH Client on the client pc.
- The SSH client will forward all the traffic through one port only (usually 22) to the SSH server on the remote SSH server.
- The SSH server will forward all the traffic to the VNC or Remote Desktop servers.
Maybe an image is more clear:
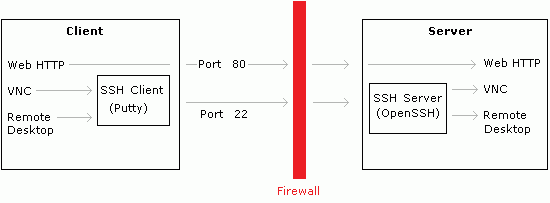
Some ports typically open are the number 21 (FTP), 22 (SSH), 23 (Telnet), 8080 (router administration), 443 (HTTPS), 110 (POP3), 25 (SMTP), and others.
If on your computer there isn't any webserver running you can use also the port number 80, but this option should be avoided, as it might cause some problems.
Step 1: Installation ans usage of an SSH terminal session
You first must realize an SSH connection between the client and the server. Have a look to
Install and use an SSH server on Windows for this phase.
Step 2: Use of the SSH Tunnel with VNC or Microsoft Remote Desktop
- In Putty, select Connection, SSH, Tunnels. Insert these values:
Source port: a random port not used on the client. For example 1234 or 5678. These are the ports that Putty will make available on the client for VNC Viewer or Remote Desktop Client.
Destination: the address and the port for the OpenSSH server of the VNC Server and Remote Desktop Server. In this case, since OpenSSH is executed on the same VNC Server, insert the loopback address (that is, the address identifying the pc itself), and the port used by VNC or RDP. Therefore: 127.0.0.1:5900 or 127.0.0.1:3389.
Select also the option Local.
- Start this Putty session.
Let's resume what you did: you created a protected connection using the SSH protocol between the client PC(where there are Putty, VNC Viewer and Remote Desktop Client) and the server(where there are OpenSSH server, VNC server and Remote Desktop Server). Moreover allowing the data exchange between the two pcs, OpenSSH moved the server ports (5900 and 3389) to the client (ports 1234 and 5678) through the port 22. Now the server ports 5900 and 3389 are available on the client, and are the 1234 and 5678.
- Start VNC (or Remote Desktop Client) on the client computer. Write the address 127.0.0.1:1234 (since that the port 1234 is available on the client itself). VNC Viewer should connect correctly to the server. The same thing is valid with the port 5678 for Remote Desktop.
NOTE: Remote Desktop Client doesn't allow, by default, the loopback connections. To work around this problem you can choose to use a non standard port, as 127.0.0.1:5678 in this guide
